 Server
Colocation
Server
Colocation
 CDN
Network
CDN
Network
 Linux Cloud
Hosting
Linux Cloud
Hosting
 VMware Public
Cloud
VMware Public
Cloud
 Multi-Cloud
Hosting
Multi-Cloud
Hosting
 Cloud
Server Hosting
Cloud
Server Hosting
 Kubernetes
Kubernetes
 API Gateway
API Gateway


As companies more and more start using cloud services it is important to have a secure public cloud infrastructure. It offers numerous advantages:
- Scalability
- Cost efficiency
- Accessibility
However, it comes with a new form of security threats as well. Below are detailed guidelines and recommendations on efficiently protecting the public cloud environment.
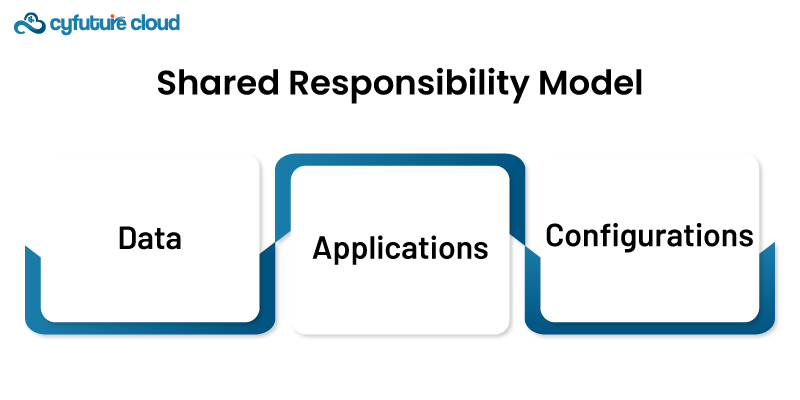
It is the basis of securing your public cloud. In this model, the accountability for the security of the cloud infrastructure lies with the cloud service providers (CSP). On the other hand, customers are expected to manage:
- Data
- Applications
- Configurations
Identifying where your duties are will help in protecting your cloud environment.
Safeguarding data in the cloud involves several strategies to ensure:
- Confidentiality
- Integrity
- Availability
Encrypt data both at rest and in transit. CSPs provide various encryption tools and services, such as:
- AWS KMS
- Azure Key Vault
- Google Cloud Key Management
Classify your data based on its sensitivity and apply appropriate security controls. Sensitive information should have stricter security measures.
Data backup is advised to be frequent. A strong disaster recovery strategy should be created. Always test your backup to ensure they work as intended and are reliable.
Securing your cloud network involves implementing measures to control and monitor traffic in cloud resources.
Use VPCs to isolate your cloud resources and control their access. It allows you to
- Create private subnets
- Route tables
- Network gateways to manage traffic flow securely
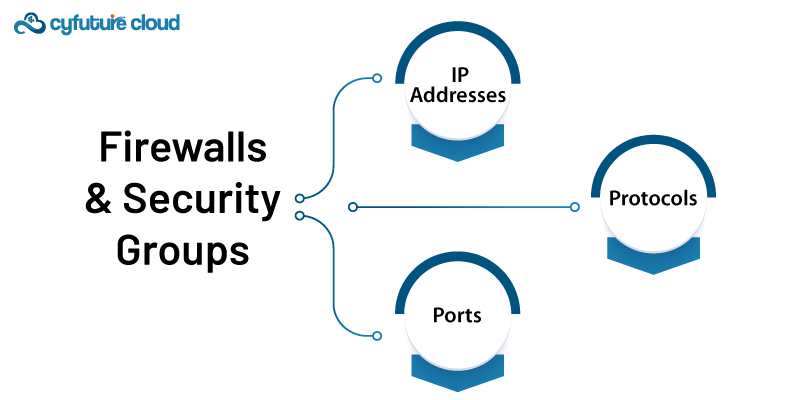
Configure security groups and firewalls to control inbound and outbound traffic. Use these tools to define rules that restrict access based on
- Protocols
- Ports
Remote access to cloud resources should be protected with VPNs. It protects the data exchanged between your corporate local area network and your cloud infrastructure.
Continuous monitoring and logging are essential for detecting and responding to security incidents.
Utilize cloud-native monitoring tools such as:
- AWS CloudWatch
- Azure Monitor
- Google Cloud Operations
These tools provide real-time insights into the performance and security of your cloud environment.
Implement centralized log management to collect and analyze logs from various sources. Numerous services help track user activities and detect suspicious behavior like:
- AWS CloudTrail
- Azure Log Analytics
- Google Cloud Logging
Deploy IDPS to identify and respond to potential threats. These systems can alert you to unusual activities and automatically block malicious traffic.
It is extremely crucial to ensure that your cloud-based resources are configured correctly and to maintain a strong security position.
Use configuration management tools to enforce compliance with security policies and best practices:
- AWS Config
- Azure Policy
- Google Cloud Asset Inventory
Check for security holes and misconfigurations on a regular basis. You can also identify any potential weaknesses through penetration tests.
Implement automated remediation to correct misbehaviors and make sure that adherence is adhered to. Tools can help automate these processes like:
- AWS Lambda
- Azure Automation
- Google Cloud Functions
Protecting your applications in the cloud involves incorporating a shield into every stage of the development lifecycle.
Follow secure development practices such as:
- Code reviews
- Static code analysis
- Threat modeling
- Security testing into your CI/CD pipeline
Deploy WAFs to protect your web applications from common attacks such as:
- SQL injection
- XSS
CSPs offer managed services that can be easily integrated with your applications.
Secure your APIs using authentication and authorization mechanisms. Implement rate limiting to prevent abuse and monitor API traffic for suspicious activities.
Adherence to industry standards and regulations is important for organizations operating in regulated environments.

Familiarize yourself with compliance frameworks relevant to your industry, such as:
- GDPR
- HIPAA
- PCI DSS
CSPs often provide tools and documentation to help you achieve and maintain compliance.
Establish governance policies that delineate how your organization manages and secures its cloud resources. These policies should cover aspects such as:
- Access control
- Incident response
A robust incident response plan is essential for quickly addressing security mishappenings and minimizing their impact. It should outline the steps to take during a security breach. The plan should include
- Roles and responsibilities
- Communication protocols
- Procedures for containment, eradication, and recovery.
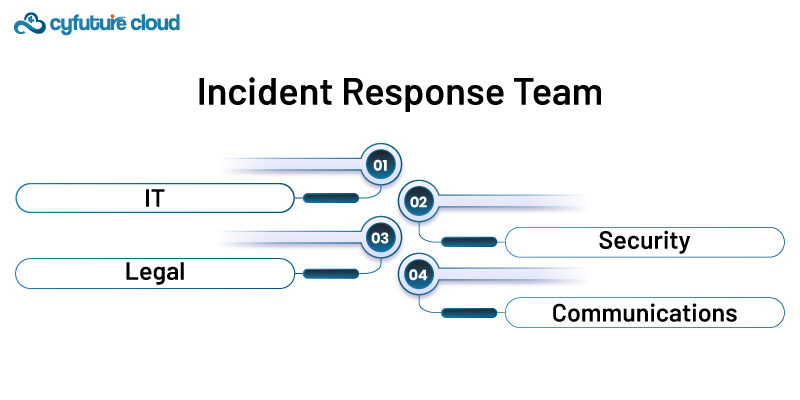
Assemble a dedicated incident response team with members from various departments.
- IT
- Security
- Legal
- Communications
Regularly train and drill the team to ensure they can handle incidents effectively.
Conduct post-incident feedback to identify lessons learned and improve your incident response capabilities. Document the findings and update your incident response plan as needed.
Some strategies that must be implemented to protect the public cloud environment include the following. Being familiar with the shared responsibility model and applying the best practices to these areas minimizes the chances of security threats. Also, you can guarantee the authenticity, confidentiality, and accessibility of the cloud resources. It is advisable to check and revise the security measures occasionally as new threats come up and the cloud environment changes.

Let’s talk about the future, and make it happen!
By continuing to use and navigate this website, you are agreeing to the use of cookies.
Find out more


