 Server
Colocation
Server
Colocation
 CDN
Network
CDN
Network
 Linux Cloud
Hosting
Linux Cloud
Hosting
 VMware Public
Cloud
VMware Public
Cloud
 Multi-Cloud
Hosting
Multi-Cloud
Hosting
 Cloud
Server Hosting
Cloud
Server Hosting
 Kubernetes
Kubernetes
 API Gateway
API Gateway


Dedicated servers are robust and flexible instruments, affording users total authority over their hosting ecosystem. Whether you're a business proprietor seeking to host a website, a developer overseeing applications, or an aficionado configuring a game server, the primary stride toward unlocking your dedicated server's complete potential is gaining access. This knowledge base resource is here to supply an exhaustive guide, beginning with the initial setup and progressing through diverse techniques for remote access and server administration.
A dedicated server is a high-performance, remote computer entirely devoted to one user or organization. These servers provide exclusive access to CPU, RAM, storage, and network resources and are ideal for hosting a wide range of applications.
Dedicated servers provide exceptional performance, extensive customization options, top-notch security, unwavering reliability, and impressive scalability. They represent a precious asset for both individuals and businesses seeking tailored hosting solutions to meet their distinct requirements.
Selecting the right server provider is crucial. Consider factors such as hardware specifications, data center locations, support options, and pricing to make an informed choice.
Dedicated servers can be set up physically or accessed remotely. Physical access involves close proximity to the server and direct interaction, while remote access enables management from anywhere with internet connectivity.
Initial hardware setup, including peripheral connections and BIOS configuration, may be required if you have physical access. For remote servers, this setup is typically managed by the hosting provider.
Most providers offer a choice of operating systems. You can install your preferred OS via remote console access or a control panel provided by your hosting company.
Before accessing your server, ensure it is secure. Basic security measures include changing default passwords, applying updates, and configuring firewalls.
In this hands-on exercise, you'll be required to establish a connection between your server and essential peripherals – a monitor, keyboard, and mouse. This setup essentially transforms your server into a regular computer, allowing you to directly interact with it. This hands-on experience provides a tangible, real-world insight into the process of managing your server.
Remote access is widely used for dedicated servers, offering flexibility and convenience.
Remote Desktop Protocol (RDP), Virtual Network Computing (VNC), and web-based control panels are common technologies for remote access. Each method facilitates remote server management.
RDP is a Microsoft protocol for remote access to Windows servers. It allows full interaction with the server's desktop environment.
VNC is a cross-platform remote desktop protocol for viewing and controlling your server's desktop from a remote location.
Web-based control panels like cPanel, Plesk, and Webmin provide server management through a user-friendly graphical interface. These panels simplify website configuration, email setup, and database management.
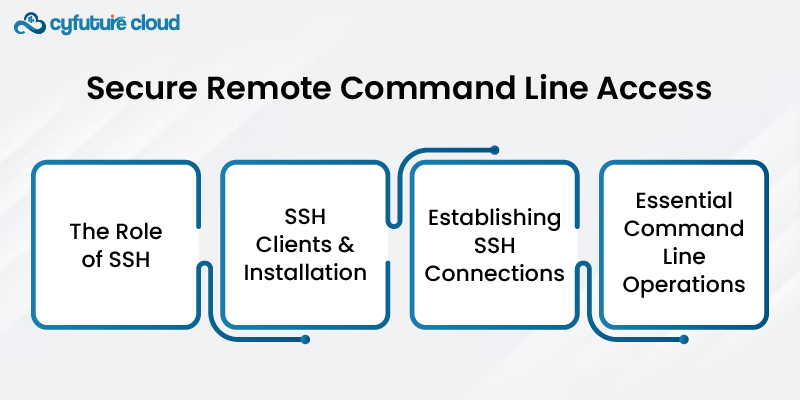
SSH, which stands for Secure Shell, is a highly favored protocol when it comes to ensuring secure remote access and the effective administration of command lines. It enhances security by facilitating encrypted communication between the client and the server, offering a robust shield against unauthorized access and data breaches.
SSH clients are accessible across a diverse array of operating systems. To establish a secure connection with your server, it's essential to have an SSH client at your disposal.
Access your dedicated server via SSH using the server's IP address and appropriate login credentials. SSH provides remote command line access.
Basic command line operations are essential for server management. They include configuring the server, installing software, and monitoring system performance.
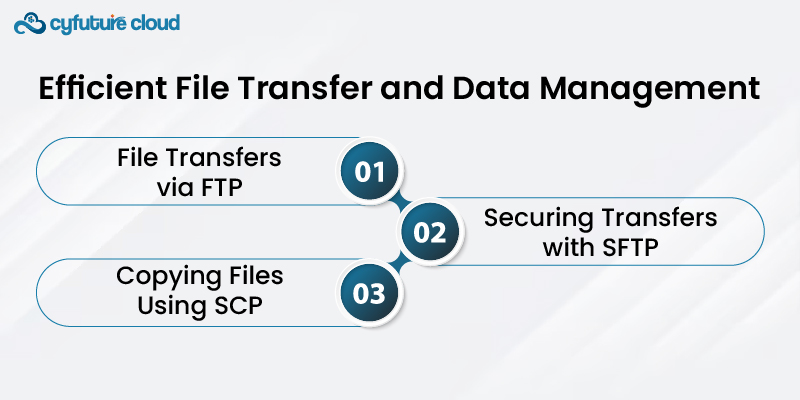
File Transfer Protocol (FTP) serves as the go-to method for moving files to and from your dedicated server. There's a multitude of FTP clients available, empowering you to effortlessly upload, download, and efficiently oversee your files.
Secure File Transfer Protocol (SFTP) is a secure alternative to FTP. It encrypts data during transfer, enhancing security. Most SSH clients support SFTP.
Secure Copy Protocol (SCP) is another secure file transfer method operating over SSH. It securely copies files between your local machine and the server.
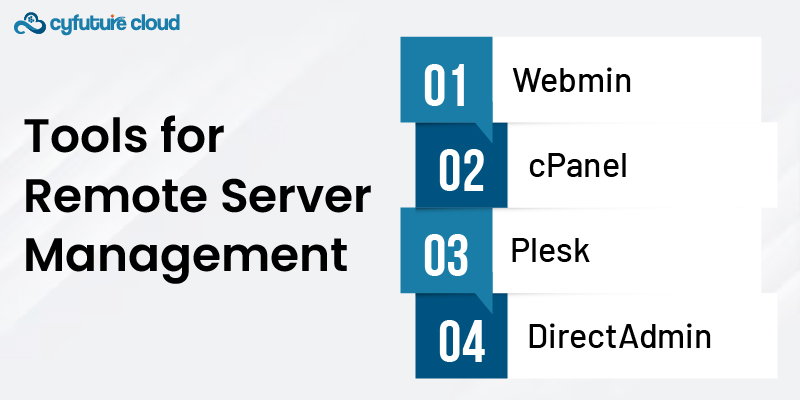
Webmin is a user-friendly web-based control panel that considerably simplifies server maintenance. It offers a user-friendly interface that makes changing system settings, managing user accounts, and administering server functions a breeze.
cPanel is a widely-used control panel for managing web hosting services. It provides tools for website administration, email setup, and database management.
Plesk is another popular web hosting control panel known for its simplicity and versatility. It caters to both Linux and Windows servers, making it a comprehensive choice.
DirectAdmin is a lightweight and efficient control panel for web hosting management. It includes features for email, databases, and website hosting.
A firewall is a crucial security measure. Configure it to filter incoming and outgoing network traffic, allowing only authorized connections.
Apply security patches and system upgrades to keep your server up to date. In addition, develop a backup policy to protect your data in the event of data loss or system failure.
Enforce strong password policies and manage user accounts carefully. Create separate accounts for different users and restrict their access as needed.
Implement multi-factor authentication for enhanced security. MFA requires users to provide two or more forms of verification before accessing the server.
If you encounter problems accessing your server, such as network connectivity issues or login problems, follow common troubleshooting steps.
Your hosting provider can offer support and assistance. Contact their support team if you encounter issues you can't resolve on your own.
Online communities and forums can be valuable resources for solving problems and sharing knowledge with other server administrators.
In conclusion, accessing your dedicated server is the initial step towards harnessing its capabilities. Whether you opt for physical or remote access, it's essential to understand the methods, tools, and best practices involved. This guide has provided insights into setting up, accessing, and securing your dedicated server, helping you make the most of this versatile hosting solution.

Let’s talk about the future, and make it happen!
By continuing to use and navigate this website, you are agreeing to the use of cookies.
Find out more


