 Server
Colocation
Server
Colocation
 CDN
Network
CDN
Network
 Linux Cloud
Hosting
Linux Cloud
Hosting
 VMware Public
Cloud
VMware Public
Cloud
 Multi-Cloud
Hosting
Multi-Cloud
Hosting
 Cloud
Server Hosting
Cloud
Server Hosting
 Kubernetes
Kubernetes
 API Gateway
API Gateway


As organizations continue to adopt cloud computing to store and process their information, there is a need for robust cloud security. It safeguards data, applications, and infrastructure against
- Threats
- Vulnerabilities
- Compliance issues
Let's explore the top cloud security solutions available today
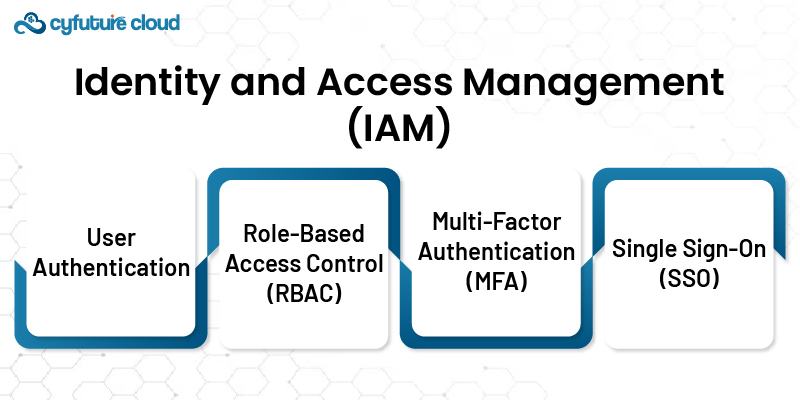
These solutions are crucial in defining the access rights of cloud resources and the permissions that come with them. It makes sure that only those who should be using certain data or applications can utilize it. Thus reducing the risk of data breaches.
1. User Authentication
Verifies the users to the cloud resources before they can access them.
2. Role-Based Access Control (RBAC)
Functionally, it provides permissions to users about their status within an organization. Thus, they will be granted the necessary access to do their work.
3. Multi-Factor Authentication (MFA)
It also enhances the security aspect. Users are required to provide several forms of identification before accessing the resources.
4. Single Sign-On (SSO)
Enables users to sign in once and be granted access to various cloud applications. It makes the user interface easier to manage and enhances security.
- Enhanced regulatory compliance to the set standards.
- The risk of insider threats and unauthorized access is minimized.
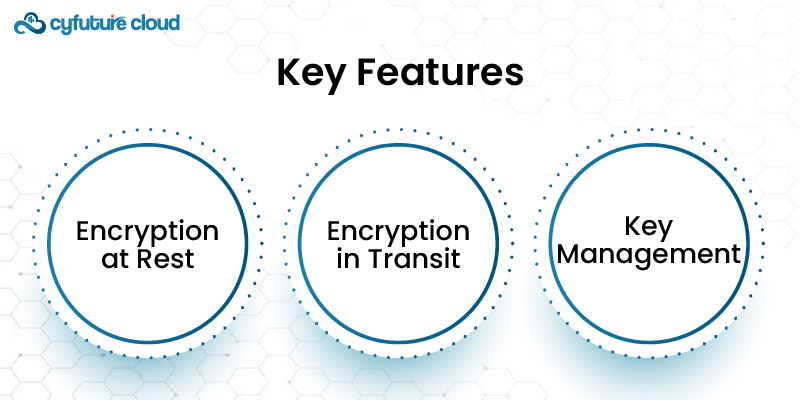
Data encryption solutions can keep certain information away from certain people. The data is encrypted and can only be interpreted by certain individuals. Encryption means that even if the data is captured or in the wrong hands, it cannot be comprehended or used as encoded.
- Encryption at Rest
Protects data stored in the cloud by encrypting it when it is not actively used.
- Encryption in Transit
Secures data as it is transmitted between cloud services and users, preventing interception during transmission.
- Key Management
Manages encryption keys securely. Thus ensuring that only authorized users can access and decrypt data.
2. Provides data security and protection.
3. It also ensures that the company complies with the legal requirements concerning data protection.
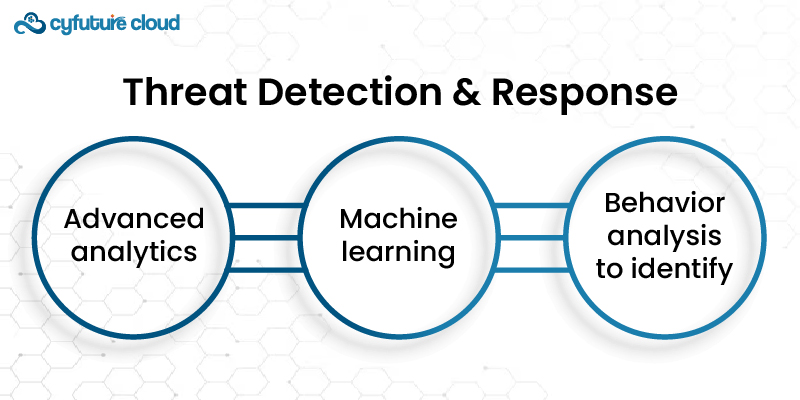
These solutions always look for hazard indications in cloud environments. It facilitates organizations to be in a position to identify threats in real-time and also contains them. Threat Detection & Response solutions help to define and prevent security breaches and other related occurrences:
- Advanced analytics
- Machine learning
- Behavior analysis to identify
Performs constant monitoring of the cloud environment and may detect suspicious activities and threats.
2. Incident Response
Allows the creation of tools and procedures for fast identification and handling security threats.
3. Behavioral Analytics
Utilizes machine learning algorithms to analyze the user activity to detect signs of a security threat.
4. Automated Threat Detection
Automatically identifies threats and notifies the security team of threats. Thus shortening response time.
- Less incidence of loss of data and other security threats.
- Increased understanding of the position in cloud security.
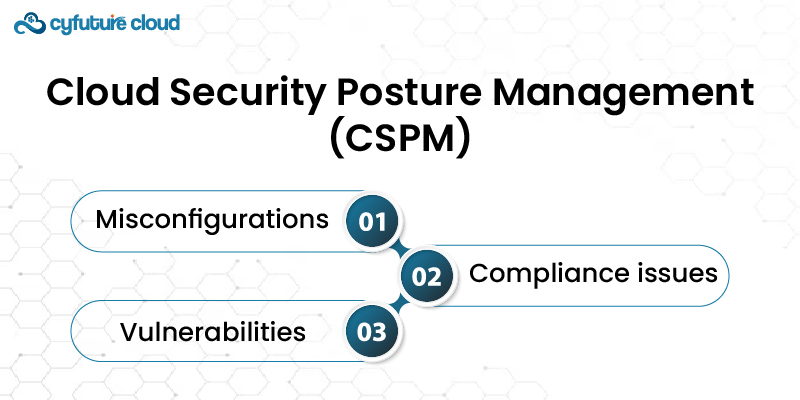
These solutions optimize an organization’s safety stance in the cloud. It continuously monitors and assesses their cloud environments. CSPM solutions identify:
- Misconfigurations
- Compliance issues
- Vulnerabilities
Thus providing recommendations for remediation.
1. Configuration Assessment
Continuously scans cloud environments for configuration issues that may expose the environment or its assets to threats.
2. Compliance Monitoring
Ensures that cloud environments comply with relevant regulatory standards and best practices.
3. Vulnerability Management
Identifies and prioritizes vulnerabilities in cloud resources. Thus helping organizations address them promptly
4. Automated Remediation
Provides automated tools for fixing security issues and improving cloud security posture.
2. Less security breaches due to misconfigurations & vulnerabilities.
3. Better adherence to the rules and guidelines governing the provision of health services.
CWPPs are solutions that offer protection for workloads that are being executed in cloud environments. These solutions help cover virtual machines, containers, and serverless workloads against threats and risks. Thus ensuring that cloud applications remain secure.
1. Workload Visibility
Offers granular insights into all cloud-based workloads such as:
- VMs
- Serverless apps.
2. Threat Detection
Prevents and detects risks to cloud workloads as they happen.
3. Vulnerability Management
It scans the workload for vulnerabilities and suggests how to address the issues.
4. Runtime Protection
Monitors and protects workloads during runtime, preventing attacks and unauthorized access.
- Improved visibility and control over cloud applications.
- Lesser probability of security threats and violations.
A Security Information and Event Management solution is designed to
- Gather
- Process
- Correlate security data from different sources to offer an organization’s security status.
SIEM solutions assist in identifying security threats and analyzing them in real-time to produce a response.
1. Log Collection and Analysis
Aggregates and analyzes security logs from various sources to identify potential threats.
2. Correlation and Alerting
Correlates security events and generates alerts for suspicious activities.
3. Incident Investigation
Provides tools for investigating security incidents and identifying root causes.
4. Compliance Reporting
Prepares reports to show that it has complied with the rules and regulations and the standards set in the market.
- Better awareness of security events and incidents.
- Improved threat detection & response capabilities.
- Support for regulatory compliance and reporting.
Ensuring robust security in cloud environments is critical for:
- Protecting sensitive data
- Maintaining regulatory compliance
- Safeguarding business operations
Above, we have defined the top cloud security solutions available today. Each solution addresses specific security challenges and provides unique benefits. It helps an organization to develop a holistic and sound cloud security plan. Enterprises can improve their security and protect the cloud services through these solutions.

Let’s talk about the future, and make it happen!
By continuing to use and navigate this website, you are agreeing to the use of cookies.
Find out more


