 Server
Colocation
Server
Colocation
 CDN
Network
CDN
Network
 Linux Cloud
Hosting
Linux Cloud
Hosting
 VMware Public
Cloud
VMware Public
Cloud
 Multi-Cloud
Hosting
Multi-Cloud
Hosting
 Cloud
Server Hosting
Cloud
Server Hosting
 Kubernetes
Kubernetes
 API Gateway
API Gateway


In this particular knowledge base post, several fundamental elements of maintaining data privacy within the cloud settings will be discussed. First, we will expound on emergent risks that are inherent in the body of knowledge protection in these settings as well as possible compliance.
Next, we will discuss the solutions to improve confidentiality expected in the near future frameworks, such as encryption methods, access controls, and compute enclaves. Last but not least, we shall offer you a checklist of best practices and recommendations for implementing the cloud to enhance the privacy and security of your data as you transform your business’s IT infrastructure.
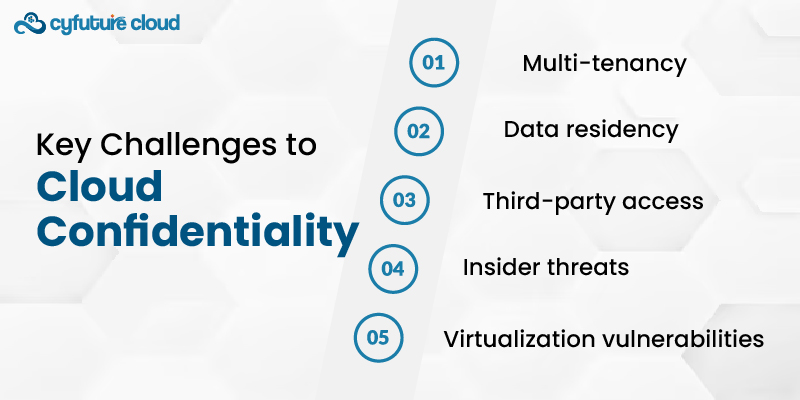
1. Multi-tenancy: Multiple customers can be hosted on a public cloud, which shares the infrastructure; issues of data isolation and breaches may arise.
2. Data residency: Some cloud providers may store information in different sites, thereby raising the issue of compliance with data protection laws.
3. Third-party access: The client’s data could be visible to cloud hosting providers and their employees, violating confidentiality.
4. Virtualization vulnerabilities: These and other vulnerabilities found in hypervisors or virtual machine management could result in crossing from one tenant to another.
5. Insider threats: The threat that comes with these threat actors is the people within the cloud provider’s organization with ill intent of denying data confidentiality.
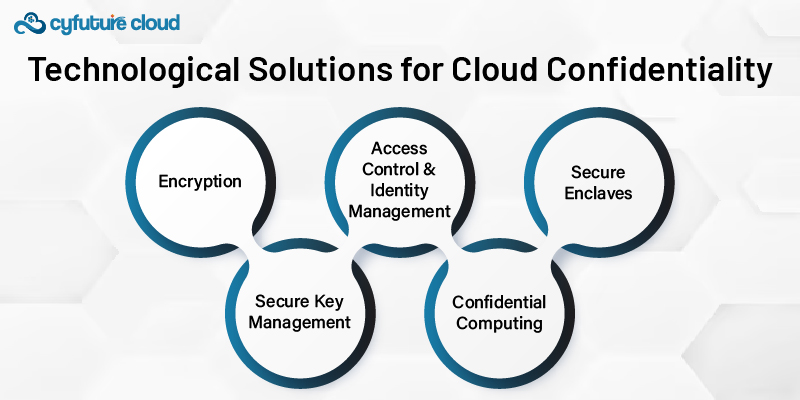
1. Encryption
Encryption is a fundamental technique for protecting data confidentiality in the cloud. It includes:
- Data-at-rest encryption
- Data-in-transit encryption
- Client-side encryption
2. Secure Key Management
Proper key management is crucial for effective encryption:
Physical devices known as Hardware Security Modules (HSMs) are used to produce, store, and manage encryption keys safely.
- Key Management Services (KMS): Cloud-based programs that rotate and manage keys centrally.
3. Access Control and Identity Management
Robust access controls help maintain confidentiality:
- Multi-factor authentication (MFA): Demanding many verification methods in order to grant access to a user.
- Role-based access control, or RBAC: Restricting access to data according to the roles and responsibilities of users.
- Just-in-time (JIT) access: Providing resources with brief, time-limited access.
4. Confidential Computing
Emerging technologies protect data during processing:
- Secure code execution in isolated settings is possible with Trusted Execution settings (TEEs).
- Encrypted data may be computed using homomorphic encryption without the need for decryption.
5. Secure Enclaves
For critical processes, secured memory areas are created using hardware-based isolation methods like AMD SEV or Intel SGX.

1. Shared Responsibility Model
Understand the division of security responsibilities between the cloud provider and customer. Typically, the provider secures the underlying infrastructure, while customers are responsible for protecting their data and applications.
2. Data Classification and Handling
Implement a robust data classification system to identify sensitive information and apply appropriate security controls based on data criticality.
3. Encryption Strategy
Develop a comprehensive encryption strategy covering data at rest, in transit, and potentially in use. Use strong, industry-standard encryption algorithms and protocols.
4. Key Management
Implement a secure key management system, including regular key rotation and secure backup procedures. Consider using cloud provider key management services or third-party solutions.
5. Access Control and Monitoring
Enforce the principle of least privilege, granting users only the minimum necessary access. Implement strong authentication methods and continuously monitor access patterns for anomalies.
6. Vendor Assessment and Compliance
Cautiously assess security measures , certifications and compliance of cloud providers with the applicable standards which are the ISO 27001, SOC 2 and GDPR. Check that they’ve ensured the appropriate levels of confidentiality in service level agreements (SLAs).
7. Security Audit Test and Vulnerability Assessment
Carry out regular security audits to enable the identification of some of the gaps in the system and the efficiency of the confidentiality measures to be determined.
8. Employee Training and Awareness
Train employees to understand the do’s and don’ts of cloud security, ways through which data should or should not be handled, and their responsibilities related to security.
9. Incident Response Planning
Create and rehearse a Cloud-Specific Incident Handling Plan that covers actions to take in the case of a possible confidentiality compromise.
10. Data Residency and Sovereignty
Understand that some data must reside in certain locations due to regulatory requirements and use feature of a cloud provider if there is need to control data location.
Like other aspects of using public cloud environments, data confidentiality remains a specific challenge that can, however, be managed through technological solutions and best practices. This implies that organizations should address strong encryption and adhere to industry best practices and access controls to enhance confidentiality in public clouds.
However, it is important for one to note that cloud security is a continuous procedure. Since threats are constantly changing and new technologies are being developed, it is crucial to constantly review and improve the confidentiality level. This way, the public cloud becomes a viable option that even businesses holding sensitive data can use with security gaps left effectively unprotected.

Let’s talk about the future, and make it happen!
By continuing to use and navigate this website, you are agreeing to the use of cookies.
Find out more


