 Server
Colocation
Server
Colocation
 CDN
Network
CDN
Network
 Linux Cloud
Hosting
Linux Cloud
Hosting
 VMware Public
Cloud
VMware Public
Cloud
 Multi-Cloud
Hosting
Multi-Cloud
Hosting
 Cloud
Server Hosting
Cloud
Server Hosting
 Kubernetes
Kubernetes
 API Gateway
API Gateway


Ever wondered why your favorite websites or applications sometimes become sluggish or unreachable? It could be due to a DDoS attack. A DDoS, or Distributed Denial of Service attack, is like a massive digital traffic jam where a flood of bogus requests overwhelms a website, server, or network, disrupting its normal functioning.
Understanding "how does DDoS work" is essential because these attacks can lead to significant consequences, including downtime, financial losses, and reputational damage. So, "what is DDoS and how does it work?" Essentially, a DDoS attack floods the target with excessive traffic, making it difficult for legitimate users to access services.
Let's explore in more detail "how DDoS attack works" to help organizations defend against such threats effectively.
Let’s get started!
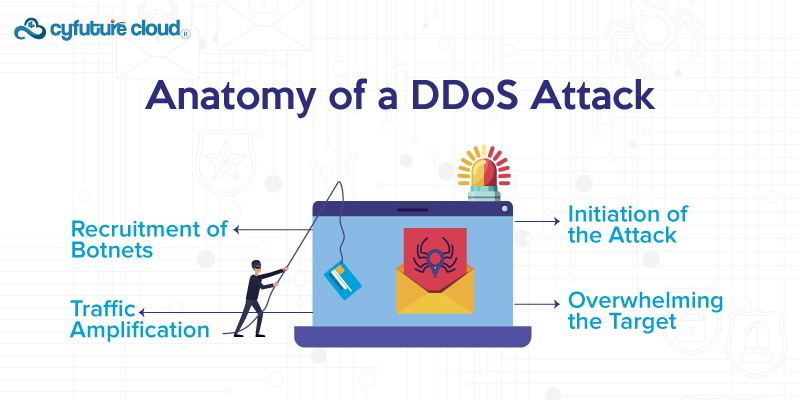
1. Recruitment of Botnets
Distributed Denial of Service attacks are carried out through botnets, networks, and compromised devices. These units of hardware range from computers and servers to Internet of Things (IoT) devices, and even smartphones are infected with malware, making them susceptible to remote control by an attacker.
The attacker then recruits these devices into a botnet, often without their owners ever knowing what is happening. Thus, this potent pack of hijacked systems is ready to unleash an assault.
2. Initiation of the Attack
When the botnet is established, then an attacker launches a DDoS attack by issuing commands to compromised devices that amplify these massive volumes of traffic back to their target.
This surge of traffic is often in the form of HTTP requests, UDP (user datagram protocol) packets, or other network protocols based on the type of attack.
3. Traffic Amplification
There is a certain strategy called amplification which, in some cases, allows attackers to increase the amount of directed traffic per unit and then target as a result. DNS amplification, in which the attacker spoofs the victim with a forged source IP address and sends double requests to servers that are configured as domain name resolvers, is one of them.
The servers then replay the traffic to the spoofed IP address with much bigger responses, thereby increasing the amount of traffic heading toward the target.
4. Overwhelming the Target
The target is inundated with vast amounts of traffic that its resources, such as bandwidth or processing power, cannot handle, which precludes the ability to answer legitimate requests from users.
Therefore, the victim suffers performance loss, slowness, or even total unavailability, which results in a denial of service to legitimate users trying to use that website or service.

|
Types of DDoS Attacks |
Purpose |
Volumetric Attacks |
Volumetric DDoS attacks aim to flood the target with massive traffic, completely saturating all available bandwidth and resources. Such attacks are often carried out using botnets and generate large amounts of garbage traffic. They may include UDP or ICMP (Internet Control Message Protocol) packets. |
Application Layer Attacks |
Application layer (Layer 7) DDoS attacks focus on specific weaknesses in web applications or services, aiming to deplete server resources or interfere with application operation. Such attacks are often clouded with legitimate user traffic to escape detection. Some examples of application layer attacks are HTTP flooding, Slowloris attack, and SQL injection. |
Protocol Attacks |
DDoS attacks based on protocols are designed to exploit weaknesses in network protocols or services that typically lead to interruption or resource depletion. These attacks can take advantage of vulnerabilities in TCP/IP, DNS, or other protocols used by the network. The protocol attacks include SYN floods, ACK floods, and TCP fragmentation attacks. |
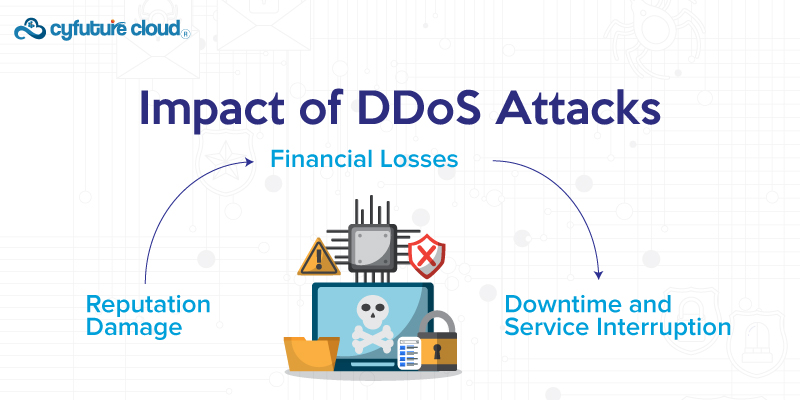
1. Downtime and Service Interruption
The aim of DDoS attacks is to make the system fail or suspend normal operations. This downtime can be very expensive for businesses. As it results in loss of revenue, tarnished reputation, and dissatisfied customers.
2. Financial Losses
Businesses can incur large sums of money due to DDoS attacks. It includes the costs associated with fighting back such an attack, lost sales during downtime, and possible fines or penalties for failure.
3. Reputation Damage
The effect of downtime can cause serious damage to a client’s reputation. In addition, a data breach can cause long-term consequences. Thus may result in a loss of trust from customers.

1. DDoS Mitigation Solutions
However, real-time detection and mitigation of DDoS attacks are feasible by using dedicated hardware appliances or cloud-based DDoS protection services as the implemented Cloud solutions for dealing with such threats.
These mitigation strategies implement traffic scrubbing, rate limiting and IP filtering to identify malicious traffic that is isolated while allowing legitimate one through.
2. Network Security Best Practices
The adoption of network security best practices, such as using firewalls, IDS/IPS, and periodic security audits. It can help organizations detect DDoS attacks before they reach their target.
3. Anomaly Detection and Traffic Monitoring.
The use of anomaly detection systems and continuous monitoring to track traffic can enable organizations to detect abnormal patterns or spikes in the flow network as a sign that there is an impending DDoS attack.
Early detection allows organizations to take precautions and minimize the impact of an attack on service availability.
4. Cooperative and Information Exchange.
Nevertheless, cybersecurity organizations can enhance their ability to identify and respond to DDoS attacks. Through information sharing with industry peers as well as threat intelligence.
It enables enterprises to stay informed of the latest threats and be able to take preventative measures against DDoS attacks.
In a nutshell, DDoS attacks pose a significant threat to an organization's online presence. Further, it can cause downtime, financial losses, and reputation damage.
By adopting a proactive approach to DDoS defense organizations can mitigate the risk of DDoS attacks and safeguard their digital assets.

Let’s talk about the future, and make it happen!
By continuing to use and navigate this website, you are agreeing to the use of cookies.
Find out more


