Get 69% Off on Cloud Hosting : Claim Your Offer Now!
- Products
-
Compute
Compute
- Predefined TemplatesChoose from a library of predefined templates to deploy virtual machines!
- Custom TemplatesUse Cyfuture Cloud custom templates to create new VMs in a cloud computing environment
- Spot Machines/ Machines on Flex ModelAffordable compute instances suitable for batch jobs and fault-tolerant workloads.
- Shielded ComputingProtect enterprise workloads from threats like remote attacks, privilege escalation, and malicious insiders with Shielded Computing
- GPU CloudGet access to graphics processing units (GPUs) through a Cyfuture cloud infrastructure
- vAppsHost applications and services, or create a test or development environment with Cyfuture Cloud vApps, powered by VMware
- Serverless ComputingNo need to worry about provisioning or managing servers, switch to Serverless Computing with Cyfuture Cloud
- HPCHigh-Performance Computing
- BaremetalBare metal refers to a type of cloud computing service that provides access to dedicated physical servers, rather than virtualized servers.
-
Storage
Storage
- Standard StorageGet access to low-latency access to data and a high level of reliability with Cyfuture Cloud standard storage service
- Nearline StorageStore data at a lower cost without compromising on the level of availability with Nearline
- Coldline StorageStore infrequently used data at low cost with Cyfuture Cloud coldline storage
- Archival StorageStore data in a long-term, durable manner with Cyfuture Cloud archival storage service
-
Database
Database
- MS SQLStore and manage a wide range of applications with Cyfuture Cloud MS SQL
- MariaDBStore and manage data with the cloud with enhanced speed and reliability
- MongoDBNow, store and manage large amounts of data in the cloud with Cyfuture Cloud MongoDB
- Redis CacheStore and retrieve large amounts of data quickly with Cyfuture Cloud Redis Cache
-
Automation
Automation
-
Containers
Containers
- KubernetesNow deploy and manage your applications more efficiently and effectively with the Cyfuture Cloud Kubernetes service
- MicroservicesDesign a cloud application that is multilingual, easily scalable, easy to maintain and deploy, highly available, and minimizes failures using Cyfuture Cloud microservices
-
Operations
Operations
- Real-time Monitoring & Logging ServicesMonitor & track the performance of your applications with real-time monitoring & logging services offered by Cyfuture Cloud
- Infra-maintenance & OptimizationEnsure that your organization is functioning properly with Cyfuture Cloud
- Application Performance ServiceOptimize the performance of your applications over cloud with us
- Database Performance ServiceOptimize the performance of databases over the cloud with us
- Security Managed ServiceProtect your systems and data from security threats with us!
- Back-up As a ServiceStore and manage backups of data in the cloud with Cyfuture Cloud Backup as a Service
- Data Back-up & RestoreStore and manage backups of your data in the cloud with us
- Remote Back-upStore and manage backups in the cloud with remote backup service with Cyfuture Cloud
- Disaster RecoveryStore copies of your data and applications in the cloud and use them to recover in the event of a disaster with the disaster recovery service offered by us
-
Networking
Networking
- Load BalancerEnsure that applications deployed across cloud environments are available, secure, and responsive with an easy, modern approach to load balancing
- Virtual Data CenterNo need to build and maintain a physical data center. It’s time for the virtual data center
- Private LinkPrivate Link is a service offered by Cyfuture Cloud that enables businesses to securely connect their on-premises network to Cyfuture Cloud's network over a private network connection
- Private CircuitGain a high level of security and privacy with private circuits
- VPN GatewaySecurely connect your on-premises network to our network over the internet with VPN Gateway
- CDNGet high availability and performance by distributing the service spatially relative to end users with CDN
-
Media
-
Analytics
Analytics
-
Security
Security
-
Network Firewall
- DNATTranslate destination IP address when connecting from public IP address to a private IP address with DNAT
- SNATWith SNAT, allow traffic from a private network to go to the internet
- WAFProtect your applications from any malicious activity with Cyfuture Cloud WAF service
- DDoSSave your organization from DoSS attacks with Cyfuture Cloud
- IPS/ IDSMonitor and prevent your cloud-based network & infrastructure with IPS/ IDS service by Cyfuture Cloud
- Anti-Virus & Anti-MalwareProtect your cloud-based network & infrastructure with antivirus and antimalware services by Cyfuture Cloud
- Threat EmulationTest the effectiveness of cloud security system with Cyfuture Cloud threat emulation service
- SIEM & SOARMonitor and respond to security threats with SIEM & SOAR services offered by Cyfuture Cloud
- Multi-Factor AuthenticationNow provide an additional layer of security to prevent unauthorized users from accessing your cloud account, even when the password has been stolen!
- SSLSecure data transmission over web browsers with SSL service offered by Cyfuture Cloud
- Threat Detection/ Zero DayThreat detection and zero-day protection are security features that are offered by Cyfuture Cloud as a part of its security offerings
- Vulnerability AssesmentIdentify and analyze vulnerabilities and weaknesses with the Vulnerability Assessment service offered by Cyfuture Cloud
- Penetration TestingIdentify and analyze vulnerabilities and weaknesses with the Penetration Testing service offered by Cyfuture Cloud
- Cloud Key ManagementSecure storage, management, and use of cryptographic keys within a cloud environment with Cloud Key Management
- Cloud Security Posture Management serviceWith Cyfuture Cloud, you get continuous cloud security improvements and adaptations to reduce the chances of successful attacks
- Managed HSMProtect sensitive data and meet regulatory requirements for secure data storage and processing.
- Zero TrustEnsure complete security of network connections and devices over the cloud with Zero Trust Service
- IdentityManage and control access to their network resources and applications for your business with Identity service by Cyfuture Cloud
-
-
Compute
- Solutions
-
Solutions
Solutions
-
 Cloud
Hosting
Cloud
Hosting
-
 VPS
Hosting
VPS
Hosting
-
GPU Cloud
-
 Dedicated
Server
Dedicated
Server
-
 Server
Colocation
Server
Colocation
-
 Backup as a Service
Backup as a Service
-
 CDN
Network
CDN
Network
-
 Window
Cloud Hosting
Window
Cloud Hosting
-
 Linux
Cloud Hosting
Linux
Cloud Hosting
-
Managed Cloud Service
-
Storage as a Service
-
 VMware
Public Cloud
VMware
Public Cloud
-
 Multi-Cloud
Hosting
Multi-Cloud
Hosting
-
 Cloud
Server Hosting
Cloud
Server Hosting
-
 Bare
Metal Server
Bare
Metal Server
-
 Virtual
Machine
Virtual
Machine
-
 Magento
Hosting
Magento
Hosting
-
Remote Backup
-
 DevOps
DevOps
-
 Kubernetes
Kubernetes
-
 Cloud
Storage
Cloud
Storage
-
NVMe Hosting
-
 DR
as s Service
DR
as s Service
-
-
Solutions
- Marketplace
- Pricing
- Resources
- Resources
-
By Product
Use Cases
-
By Industry
- Company
-
Company
Company
-
Company
How to Deploy Cloud Using SSH Key Authentication
Table of Contents
- Introduction
- SSH Key
- The History of The SSH Protocol
- SSH Protocol
- SSH Techniques
- Public & Private Key Uses
- How User Keys Work
- Step by Step Instructions to Create an SSH Key
- Generate SSH Keys Directly from different Operating Systems: –
- Cyfuture Cloud Server Login Via SSH Keys
- Windows Linux Subsystem
- Conclusion
Introduction
Cyfuture Cloud offers two types of methods for authenticating. The most commonly used authentication is the password. But nowadays companies prefer to use SSH keys to login into the cloud. As it offers much better security than passwords. Before jumping into the generation of the SSH keys. Let us understand what exactly is SSH key.
SSH Key
An SSH key is an entrance accreditation for the SSH (secure shell) network convention. By verifying and encoding secure organization convention utilizes for distant correspondence between machines on an unstable open organization. SSH utilizes for remote document move, network the executives, and remote working framework access. The SSH abbreviation is additionally used to depict a bunch of instruments that use to connect with the SSH convention.
SSH utilizes a couple of keys to start a protected handshake between remote gatherings. The key pair holds a private and public key. The private versus public classification can be confounding as they are both called keys. It is more useful to consider the public key as a “lock” and the private key as a “key”. You give the public ‘lock’ to remote gatherings to scramble or ‘lock’ information. This information opens with the ‘private’ key which you hold in a safe spot. So how has SSH protocol evolved?
The History of The SSH Protocol
The main form of the SSH convention creates in the mid-year 1995 by Tatu Ylonen. Tatu was an analyst at the University of Helsinki while a sniffing assault was found on the college organization. A sniffing assault catches and logs the traffic that happens in an organization and can give assailants usernames and passwords which can utilize to get to basic IT resources.
A great many certifications affect, including those having a place with local area organizations. This sniffing assault propelled Tatu to sort out some way to make networks safer, and this, at last, prompted the production of the SSH convention (SSH.com).
SSH Protocol
Today, the SSH convention is known as login from a distance from one framework into another. And its solid encryption makes it ideal to complete errands like giving remote orders and remotely overseeing network and other essential framework parts. This is particularly significant in the time of cloud foundation and remote work.
To utilize the SSH, several bits of programming should be introduced. The distant frameworks need to have a piece of programming called an SSH daemon, and the framework used to give orders and deal with the far off servers necessities to have a piece of programming called the SSH client. These bits of programming are important to make an appropriate correspondence channel utilizing the SSH convention (DigitalOcean).
SSH Techniques
SSH keys are a validation technique used to get sufficiently close to a scrambled association among frameworks and afterwards eventually utilize that association to deal with the far off framework.
These keys offer a significantly safer method for signing in to your server than a perplexing secret key. SSH key approval requires two parts: a private key utilizes by the client interfacing with your example and a public key put away on your case. During the login cycle. Moreover, the server confirms on the off chance that the two keys match and awards access assuming the private key is right.
SSH keys utilize incredibly complex encryption techniques that are for all intents and purposes difficult to break utilizing savage power strategies.
As well as bringing greater security, utilizing SSH keys makes your life more straightforward: there is a compelling reason need to type or recollect passwords. Simply associate with your occurrence utilizing your private key and you are promptly signed in. However, assuming you need it, you can likewise get your SSH keys utilizing a secret word with the goal that nobody can interface with your example by taking your private key
Public & Private Key Uses
An SSH key depends upon the utilization of two related keys, a public key and a private key, that together make a key pair that utilizes the solid access certification. The private key is confidential, known distinctly to the client, and ought to encode and put away securely. The public key share unreservedly with any SSH server to which the client wishes to interface. These keys are typically overseen by an association’s IT group, or even better, with the assistance of a confided in Certificate Authority (CA) to guarantee they are put away securely.
To make the advanced character, general society and private key produce, and the pair relate to one another utilizing a solid public key cryptography calculation. Moreover, numerical calculations used to create the keys are Rivest-Shamir-Adleman (RSA) and Elliptic Curve Digital Signature Algorithm (ECDSA).
These calculations utilize different calculation strategies to produce irregular numeric blends of fluctuating length so they cannot take advantage of a savage power assault. The vital size or spot length of SSH keys decides the strength of insurance. However, 2048-piece RSA keys or 521-piece ECDSA keys offer adequate cryptographic solidarity to hold programmers back from breaking the calculation.
How User Keys Work
In a client key set. firstly the private key remaining parts of the framework uses to get to the far off framework (for example the client’s work area or PC) and uses to decode data that trades in the SSH convention. Secondly, private keys must never transmit to anybody and ought to get on a framework. For example, the framework is gotten (full plate encryption, MFA), in the client’s ownership, and the private key gets by using a passphrase. Thirdly, a public key utilizes to scramble data that can share and utilizes by the client and the far off server. On the server end, the public key saves in a document that contains a rundown of which approves public keys. Moreover, on the client’s side.
Step by Step Instructions to Create an SSH Key
SSH keys produce through a public key cryptographic calculation, the most well-known being RSA or DSA. At an extremely undeniable level, SSH keys produce through a numerical equation that takes 2 indivisible numbers and an arbitrary seed variable to yield the general population and private keys. However, this is a one-way equation that guarantees the public key gets from the private key however the private key can’t get from the public key.
SSH keys are made utilizing a key age apparatus. The SSH order line device suite incorporates a keygen instrument. Most git facilitating suppliers offer aides on the best way to make an SSH Key.
Generate an SSH key using Puttygen while creating a new cloud on Cyfuture Cloud. Cyfuture Cloud offers an intuitive dashboard for creating and managing clouds.
- Create your account on the Cyfuture Cloud portal. Log in to your account.
- Select the operating system.
- Choose a plan.
- Choose an authentication SSH Keys.
- Click on the New SSH Keys.
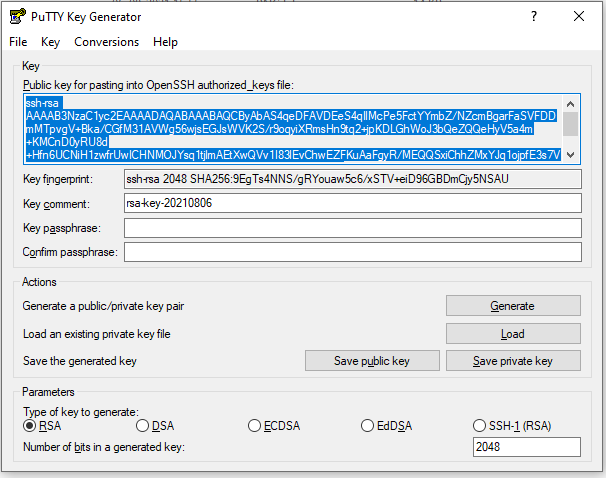
- Download Puttygen, and then start Puttygen. Generate public key and private key.
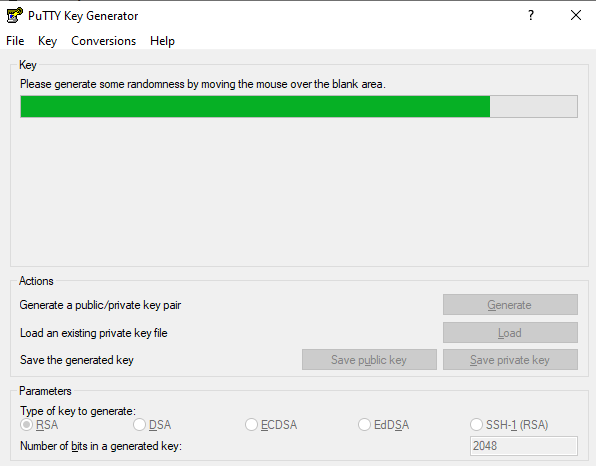
- Save the Private key and public key in your PC or MAC OS.
Generate SSH Keys Directly from different Operating Systems: –
- OR you can also use the below method to generate SSH keys.
- Open CMD in Windows, Terminal in Linux, and Terminal in Mac OSX
- Type command – ssh-keygen
- In Windows: –
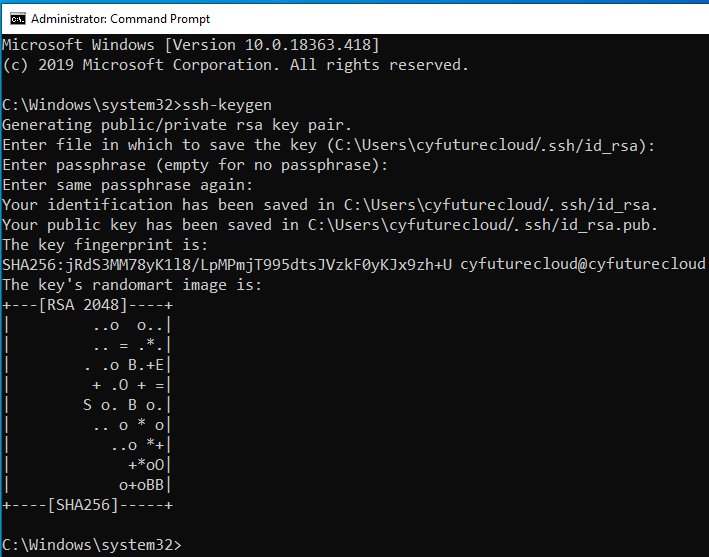
- Via Linux: –
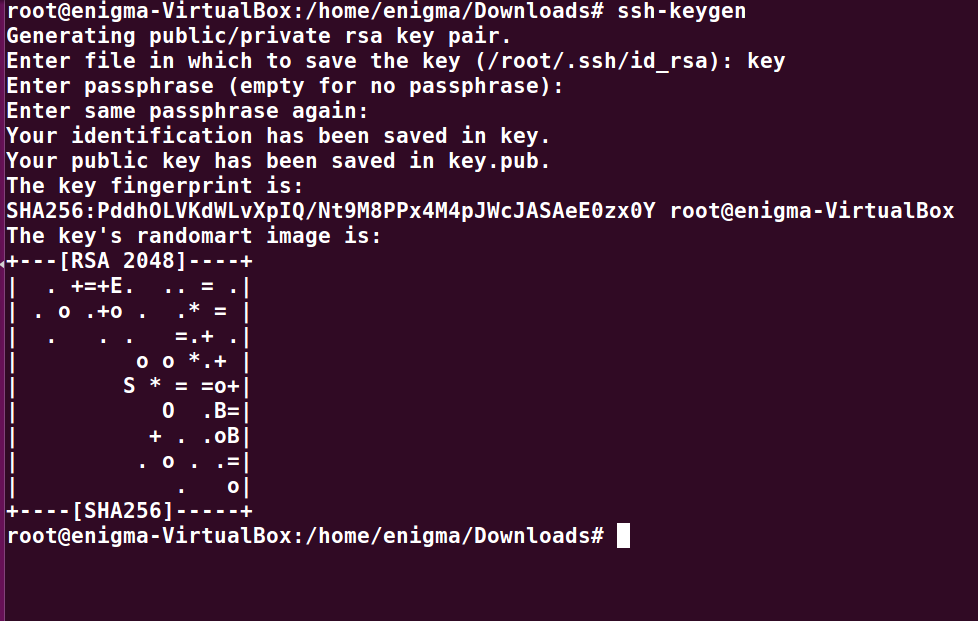
- In Mac: –
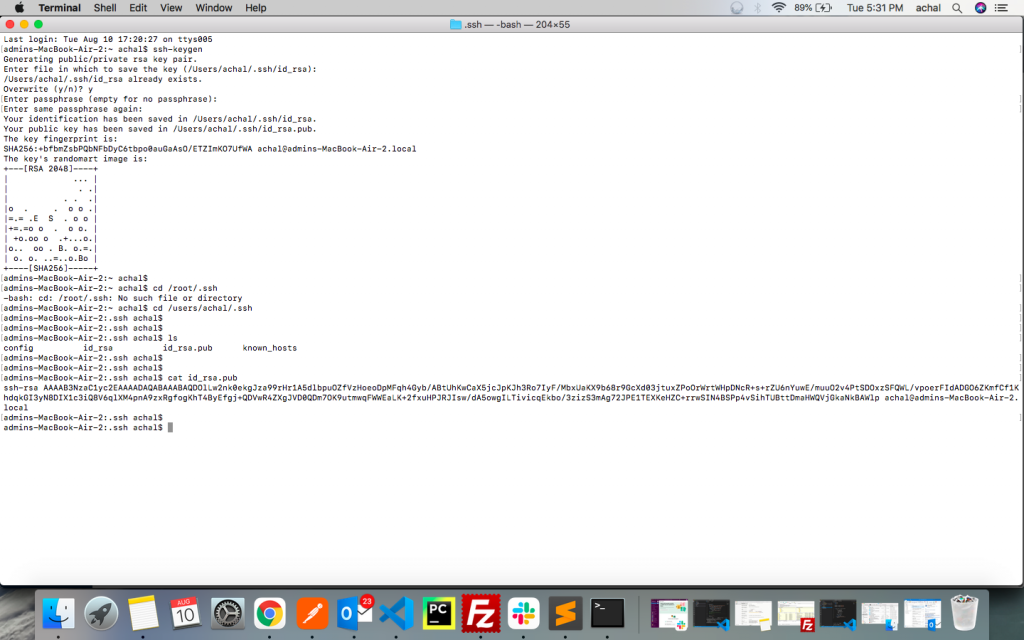
- After generating SSH-keygen
Cyfuture Cloud Server Login Via SSH Keys
- Go back to Cyfuture Cloud and configure your cloud. Paste the public SSH key in the below space.
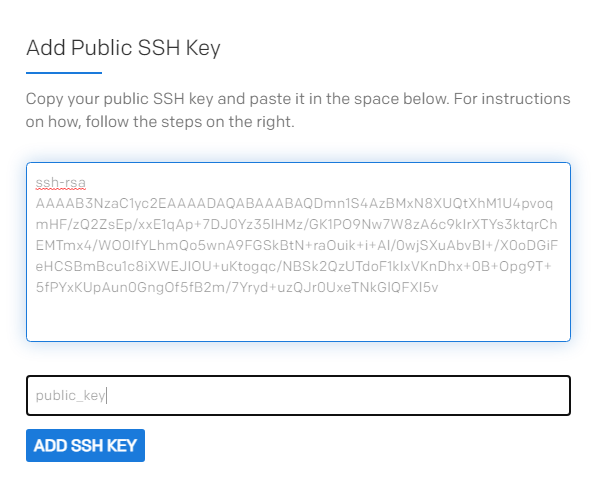
- Enter the SSH key name.
- Click on ADD SSH KEY
- Open puttygen. Enter IP address. You will receive an IP address in your email address or you can see it in the Cyfuture Cloud dashboard > My Cloud Server
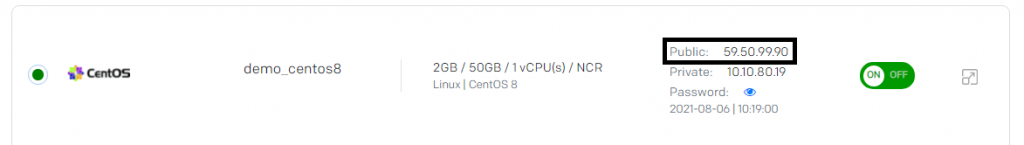
- As shown above, you can easily get the IP address.
- Firstly, Copy and paste the IP address into the Puttygen Host Name (Or IP Address)
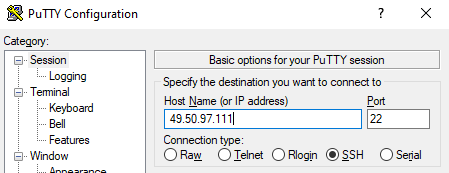
- Secondly, you have to select the location of the private key.
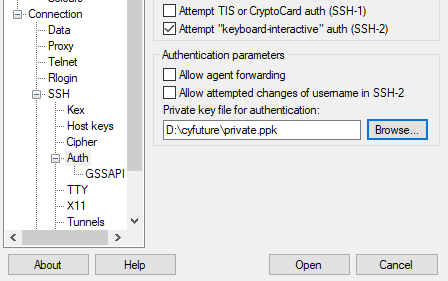
- Lastly, click on OPEN.
Windows Linux Subsystem
Initially, current windows conditions offer a windows Linux subsystem. Besides, the windows Linux subsystem offers a full Linux shell inside a conventional windows climate. Thirdly, if a Linux subsystem is accessible steps are the same for Linux cloud service. Finally, the steps for MAC are also the same within the windows Linux subsystem.
Conclusion
At last, you will directly login to your cloud. The same method will go with every operating system that you have on your Cyfuture Cloud account.
Recent Post

Stay Ahead of the Curve.
Join the Cloud Movement, today!
© Cyfuture, All rights reserved.
Send this to a friend

 Pricing
Calculator
Pricing
Calculator
 Power
Power
 Utilities
Utilities VMware
Private Cloud
VMware
Private Cloud VMware
on AWS
VMware
on AWS VMware
on Azure
VMware
on Azure Service
Level Agreement
Service
Level Agreement