Table of Contents
- The Importance of Data Security
- 1. Protection Against Data Breaches:
- 2. Upholding Privacy:
- 3. Preserving Trust:
- 4. Financial Ramifications:
- 5. Adherence to Legal and Regulatory Standards:
- 6. Safeguarding Intellectual Property:
- 7. Ensuring Availability and Reliability:
- 8. Mitigating Cybersecurity Threats:
- 9. Preserving National Security:
- 10. Peace of Mind:
- Data Security Measures
- Compliance in Colocation Hosting India
- Key Considerations When Selecting a Colocation Provider
- Choosing the Right Colocation Provider
- Conclusion
- Frequently Asked Questions
In an era where data is hailed as the new gold, businesses must place paramount importance on safeguarding sensitive information. Colocation hosting in India offers a robust solution for organizations looking to store their servers and data securely. Nonetheless, the substantial capabilities also bring significant responsibilities, and it is of the utmost importance to guarantee data security and compliance in colocation hosting.
In this blog, we’ll explore the key considerations for data security and compliance in colocation hosting facilities in India
The Importance of Data Security
The importance of data security in the current digital world cannot be emphasized. Data is more than just a valuable asset; it is frequently the lifeblood of organizations and an essential component of our personal lives. Here’s why data security matters: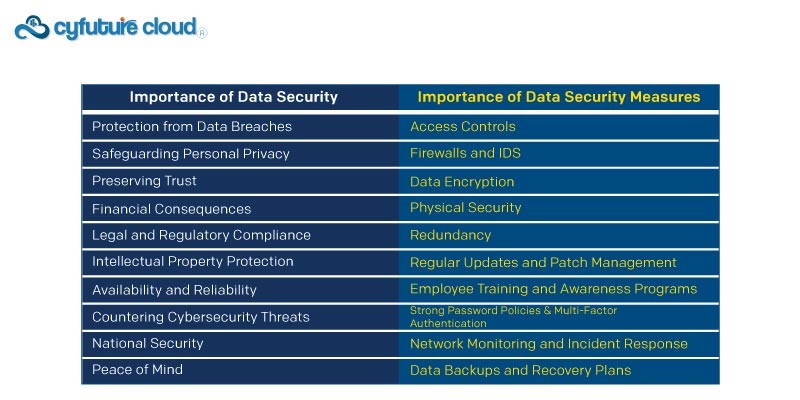
1. Protection Against Data Breaches:
Data breaches are on the increase and can have serious consequences. Unauthorized persons acquire access to sensitive information, such as personal data, financial records, or intellectual property, during a data breach. This can lead to identity theft, financial hardship, or the disclosure of sensitive corporate information. Implementing strong data security measures is crucial to prevent these breaches and safeguard both individuals and organizations from harm.
2. Upholding Privacy:
The protection of individual privacy stands as a core ethical and legal responsibility. Many regions have stringent data protection laws that necessitate businesses and organizations to take suitable measures to guard personal information. Neglecting these obligations can lead to substantial fines and legal consequences.
3. Preserving Trust:
Trust holds immense value in both personal and business relationships. When individuals entrust an entity with their data, they expect it to be handled with diligence. Data breaches have the potential to shatter this trust, causing harm to reputations and eroding people’s confidence in a company or organization.
4. Financial Ramifications:
Data breaches often come with significant costs. Apart from possible penalties for non-compliance with data protection regulations, expenses are incurred in investigating and mitigating breaches, compensating affected parties, and implementing enhanced security measures. Moreover, the loss of customers or business partners can result in enduring financial setbacks.
5. Adherence to Legal and Regulatory Standards:
Compliance with data security and privacy laws and regulations, like the European Union’s General Data Protection Regulation (GDPR) or the United States Health Insurance Portability and Accountability Act (HIPAA), demands strict adherence to precise data protection standards. Failure to comply can lead to substantial fines and penalties.
6. Safeguarding Intellectual Property:
For businesses, intellectual property, which includes trade secrets, proprietary software, and research discoveries, often holds greater value than physical assets. Data security plays a pivotal role in shielding this intellectual property from theft or espionage.
7. Ensuring Availability and Reliability:
Data security goes beyond preventing unauthorized access; it’s also about guaranteeing that data remains accessible and dependable when needed. Downtime caused by data loss, corruption, or cyberattacks can disrupt business operations, resulting in financial losses and damage to a company’s reputation.
8. Mitigating Cybersecurity Threats:
The digital landscape is rife with threats, including malware, ransomware, phishing, and denial-of-service attacks. Effective data security measures, including firewalls, intrusion detection systems, and encryption, are essential for mitigating these threats.
9. Preserving National Security:
In addition to safeguarding individual and business data, governments have a vested interest in data security. Protecting critical infrastructure, military intelligence, and sensitive government data is vital for national security.
10. Peace of Mind:
Ultimately, data security provides peace of mind to individuals and organizations. The knowledge that sensitive information is shielded from threats and that regulatory compliance is sustained allows people to concentrate on their personal or business goals without the constant concern of data breaches.
Data Security Measures
Data security is a paramount concern for any organization, especially when data is hosted off-site in colocation data centers. To ensure the protection and integrity of their data, colocation hosting providers employ a range of robust data security measures. Below, we’ll delve into these measures and explore their significance:
1. Access Controls:
Access controls are fundamental to data security in colocation hosting. These controls restrict physical access to the data center to authorized personnel only. Common access control mechanisms include biometric authentication, card-based entry systems, and video surveillance. Here’s why they are crucial:
- Preventing Unauthorized Access: Access controls ensure that only individuals with the appropriate credentials can enter the data center. This mitigates the risk of unauthorized personnel tampering with servers and data.
- Audit Trails: These controls frequently retain comprehensive logs of individuals who entered the data center and the specific times of their access. Should a security breach or data breach occur, these logs can supply vital forensic evidence.
2. Firewalls and Intrusion Detection Systems (IDS):
Firewalls and IDS play a crucial role in safeguarding data from external threats, including cyberattacks and hacking attempts. Their importance is evident in the following ways:
- Thwarting Cyberattacks: Firewalls function as protective barriers that separate a trusted internal network from an untrusted external network. They permit only authorized data traffic to traverse, thereby preventing unauthorized access. In contrast, IDS actively monitors network traffic to detect any signs of intrusion.
- Protection Against Evolving Threats: Security threats evolve rapidly. Regular updates to firewalls and IDS are essential to ensure they can detect and block new and emerging threats.
3. Encryption:
Data encryption is the practice of converting data into a code to prevent unauthorized access. In colocation hosting, data should be encrypted both in transit and at rest. The significance of encryption is evident in:
- Data Confidentiality: Even if an attacker intercepts data, encrypted data remains unintelligible without the decryption keys. This ensures data confidentiality and privacy.
- Compliance: Numerous data protection regulations and standards, including GDPR, HIPAA, and PCI DSS, require the implementation of encryption as a safeguard for sensitive data. Adhering to these compliance requirements is imperative to prevent legal consequences and financial penalties.
4. Physical Security:
Physical security measures are as crucial as digital safeguards in data centers. These measures ensure that the data center itself is physically secure. Key aspects of physical security include:
- Reinforced Infrastructure: The data center should have robust physical infrastructure, such as reinforced walls and locked cabinets, to protect against physical breaches.
- Security Personnel: Trained security personnel should be present to monitor and safeguard the data center.
- Restricted Entry Points: Entry points to the data center should be limited and controlled to prevent unauthorized access.
5. Redundancy:
Data centers implement redundancy for power and connectivity. This is significant because it ensures data availability even in adverse conditions. The importance of redundancy includes:
- Business Continuity: The presence of backup power sources and multiple network connections serves to reduce the risk of downtime. This is especially crucial for businesses that depend on uninterrupted access to their data and applications.
- Disaster Recovery: The redundancy measures in place guarantee that data remains accessible even in the face of unexpected events like power outages or network failures.
Compliance in Colocation Hosting India
- Understand Local and Global Regulations: Complying with regulations is a complex task. Familiarize yourself with India’s data protection laws, but also be aware of international regulations that might apply if your business operates globally.
- Data Classification: Classify data according to its sensitivity. This helps in implementing appropriate security measures for different types of data.
- Regular Audits and Compliance Reporting: Work with your colocation provider to conduct regular compliance audits and generate necessary reports. This is essential for demonstrating adherence to regulations.
- Employee Training: Train employees who have access to the colocation facility. They need to be aware of compliance requirements and security best practices.
Key Considerations When Selecting a Colocation Provider
When planning your approach to selecting a colocation provider, there are eight crucial factors to consider that will significantly enhance the benefits for your organization:
1. Physical Location of Colocation Facility
When deciding to opt for a colocation facility, it’s of utmost importance to carefully assess its physical location for several reasons, which include:
- Speed and User Experience: The geographic proximity of the colocation facility to your users or critical business locations can have a substantial impact on network latency, data transfer speeds, and the overall user experience.
- Disaster Recovery and Business Continuity: Choosing a provider situated in a region with a lower risk of natural disasters can reduce the likelihood of disruptions that may affect business continuity, ultimately contributing to better uptime.
- Data Security and Data Control: Selecting a provider within specific jurisdictions may be required to meet data protection regulations, compliance, and control requirements.
- Physical accessibility: What is the distance between the physical location and your IT teams? How much time will be required for them to reach the site for routine maintenance or in the case of an unexpected disruption?
2. Reliability and Uptime
Even a minimal amount of downtime can profoundly affect operations and revenue. Therefore, it’s crucial to assess the prospective colocation provider’s SLAs and track record for reliability and uptime.
During your evaluation, look for certifications such as Tier III or Tier IV data center standards, which serve as a green light in ensuring high availability and redundancy in power, cooling, and network connectivity. Opting for a provider with a well-established, reliable track record of consistently high uptime ensures that businesses can reduce the chances of service interruptions, unexpected outages, and the potential loss of data.
3. Connectivity and Network Performance
Just like downtime, unreliable connectivity and subpar network performance can cast a negative shadow on organizations. These issues directly hamper efficiency, responsiveness, and user satisfaction. By giving prominence to dependable connectivity and high-quality network infrastructure, organizations can guarantee smooth and efficient data transfer, enhanced application responsiveness, IT resilience, and an overall better user experience.
In your evaluation of colocation providers, be sure to consider their network connectivity alternatives and whether they operate as a carrier-specific or carrier-neutral data center. Opting for a provider with strong network choices can go a long way in ensuring optimal network performance and consistently low-latency connections.
4. Scalability and Flexibility
The goal of any organization is to grow, and it’s ideal to form partnerships with third parties who can keep up as you expand. Otherwise, you may have to plan a data center migration down the road if you outgrow the capabilities of the colocation provider. Therefore, consider this: will they have the capacity to support future expansion and evolving requirements? Can they readily adjust their scale, whether up or down, to meet changing needs?
To guarantee that your organization can effortlessly grow its IT infrastructure as circumstances evolve, verify that the colocation provider provides scalable infrastructure, including:
- Rack space
- Power density
- Cooling capacity
Flexibility plays a crucial role in permitting organizations to rapidly adjust and customize their colocation services to suit their specific needs during periods of growth. This includes resource allocation, contract terms, and customization options. With scalable and flexible solutions, organizations can steer clear of overprovisioning or capacity limitations, ensuring efficient resource utilization and the capability to enter the market more swiftly.
5. SLAs
Service Level Agreements (SLAs) are crucial contracts between colocation service providers and clients that outline metrics (such as uptime, availability, and response time) and the full range of services and support expected from the provider. Comprehensive SLAs (Service Level Agreements) offer a layer of accountability, guaranteeing that the provider commits to maintaining a specific standard of service quality and reliability.
Before choosing a colocation provider, it’s essential to thoroughly examine their SLAs (Service Level Agreements) with both legal and IT teams. This review ensures a clear understanding of contractual terms and formalities, including the availability of comprehensive support services such as 24/7 technical assistance and remote hands support, in addition to the expected colocation offerings. By giving priority to SLAs and robust support, organizations can be assured of the provider’s dedication to service excellence, operational reliability, and their capability to provide prompt assistance when required.
6. Security and Physical Protection
A reliable provider must implement robust security measures, including stringent access controls, comprehensive surveillance systems, and a dedicated security team, to effectively prevent unauthorized access and address physical threats. Data center facilities should adhere to recognized industry standards and certifications like SSAE 18, SOC 2, ISO 27001, and more, underscoring their strong commitment to security and compliance.
Opting for a provider with these security measures in place instills confidence in organizations regarding:
- The confidentiality, integrity, and availability of their data.
- Protection against physical attacks or breaches.
- The ability to mitigate risks linked to unauthorized access or data theft.
It’s crucial to remember that while colocation providers may offer virtual security measures, organizations should remain diligent about their security protocols unless such specifics are outlined in the Service Level Agreement (SLA). This vigilance is essential to prevent unauthorized access, data breaches, and other potential cybersecurity threats.
7. Managed Services
Is the colocation provider equipped with additional managed services for clients? By incorporating managed services, organizations can delegate certain operational responsibilities to the provider. These tasks may include hardware installation, maintenance, security updates, performance optimization, monitoring, and troubleshooting. This delegation frees up IT teams to concentrate on their core business functions while benefiting from the provider’s specialized expertise and resources.
8. Cost and Value
Cost and value serve as pivotal factors in the selection of a colocation provider as they directly influence the financial viability and return on investment for organizations. While cost is undeniably important, it is equally vital to assess the value proposition presented by the provider. A comprehensive examination of pricing models, contract terms, and cost structures enhances transparency and cost predictability. Moreover, take into account the value-added services extended by the provider, which may encompass managed services, technical support, and security measures.
By meticulously balancing costs with the overall value provided, organizations can make well-informed decisions that harmonize with their budgetary constraints. This approach ensures that the colocation provider not only meets but also effectively supports their operational requirements.
Choosing the Right Colocation Provider
Selecting the appropriate colocation provider is a crucial decision that can significantly influence your organization’s IT infrastructure’s performance, security, and scalability. By meticulously assessing the key factors mentioned above, you can make a well-informed choice tailored to your precise requirements.
At Cyfuture Cloud, we understand the criticality of colocation services and have a proven track record of delivering reliable, secure, and scalable solutions to our clients across state-of-the-art facilities. Discover further details about our colocation offerings or arrange a visit to one of our state-of-the-art data centers.
Conclusion
Colocation hosting in India is a viable option for businesses seeking a secure and compliant data storage solution. By implementing robust security measures, understanding and adhering to relevant regulations, and choosing a reputable colocation provider, businesses can ensure that their data is safeguarded and compliant with industry standards. Data security and compliance should always be at the forefront of any business’s digital strategy.

Frequently Asked Questions
1. What are the things that you need to be careful of while going for colocation hosting?
When considering colocation hosting, there are several important factors to be cautious about. Here are some key aspects to be careful of:
- Data Center Reputation
- Location
- Security Measures
- Redundancy
- Bandwidth and Connectivity
- Service Level Agreements (SLAs)
- Scalability
- Certifications
- Customer Support
- Costs and Hidden Fees
- Terms and Contracts
- Data Migration
- Backup and Disaster Recovery
- Network Providers
- Eco-Friendly Practices
2. How do you keep data safe in data centers?
The primary objective of data center security is to safeguard the servers. This involves implementing the following security measures:
- Activate services only when necessary.
- Grant access to services based on business requirements.
- Maintain systems with the latest security patches.
- Enforce robust password controls.
3. What is the difference between a managed services data center and colocation?
The primary distinction lies in server ownership. In managed hosting, you don’t own the server, whereas in colocation, you have complete ownership and control over your server, which is housed in a hosting provider’s data center. Cyfuture Cloud offers colocation hosting services in India.
4. Is a colocation provider a data processor?
The GDPR categorizes entities into two classes: data controllers and data processors. Colocation companies fall under the category of data controllers as they determine “the purposes, conditions, and means of processing personal data,” as defined by the GDPR.
5. Is a colocation data center a cloud?
The key distinction between cloud and colocation lies in data management and storage. In the cloud, the cloud provider owns servers, and data is managed virtually, similar to what Cyfuture Cloud does. In colocation, servers are not owned by the colocation facility but rather by the business that leases the space.
Recent Post
Send this to a friend

 Server Colocation
Server Colocation CDN Network
CDN Network Linux Cloud Hosting
Linux Cloud Hosting Kubernetes
Kubernetes Pricing Calculator
Pricing Calculator
 Power
Power
 Utilities
Utilities VMware Private Cloud
VMware Private Cloud VMware on AWS
VMware on AWS VMware on Azure
VMware on Azure Service Level Agreement
Service Level Agreement